Hello everyone! Sharing is caring, we are happy to share some other knowledge with you. We have prepared a Nginx guide that is divided into three series. If you already know some Nginx knowledge or want to expand your experience and cognition, this is a good fit.
We will tell you how Nginx works, what concepts it contains, how to tune Nginx to improve application performance, or how to set it up and running.
This tutorial has three parts:
Basic Concepts - This section needs to understand some of Nginx's directives and usage scenarios, inheritance models, and how Nginx chooses the server block, the order of locations.
Performance - Describes how to improve Nginx speed, and we'll talk about gzip compression, caching, buffers, and timeouts here.
SSL installation - how to configure the server to use HTTPS
To create this series, we hope that, as a reference book, you can quickly find related solutions (such as gzip compression, SSL, etc.) or read the full text directly. For better learning, we recommend that you install Nginx natively and try to practice it.
SSL and TLS
SSL (Socket Secure Layer abbreviation) is a protocol that provides a secure connection over HTTP.
SSL 1.0 was developed by Netscape but has never been publicly released due to serious security breaches. SSL 2.0 was released in 1995 and it has some problems that led to the final release of SSL 3.0 in 1996.
The first version of TLS (Transport Layer Security abbreviation) was written as an upgrade to SSL 3.0. After TLS 1.1 and 1.2 came out. Now, in the near future, TLS 1.3 is coming soon (which is really worth looking forward to) and has been supported by some browsers.
Technically, SSL and TLS are different (because each protocol describes a different version of the protocol), but many of the names used are interchangeable.
Basic SSL/TLS configuration
In order to handle HTTPS traffic, you need to have an SSL/TLS certificate. You can generate a free certificate by using Let's encrypt.
Once you have the certificate, you can easily switch to HTTPS in the following ways:
Start listening on port 443 (the default port that the browser will use when you type https://sample.co)
Provide a certificate and its key
Server {
Listen 443 ssl default_server;
Listen [::]:443 ssl default_server;
Ssl_certificate /etc/nginx/ssl/netguru.crt;
Ssl_certificate_key /etc/nginx/ssl/netguru.key;
}
We also want to achieve this by adjusting the configuration:
Use only the TLS protocol. All SSL versions will no longer be used due to well-known vulnerabilities
Use a predefined secure server password (similar to the protocol case - only a few passwords are considered safe in those days)
Keep in mind that the above settings are always changing. It is a good idea to re-update from time to time.
Ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
Ssl_ciphers EECDH+CHACHA20:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:!MD5;
Ssl_prefer_server_ciphers on;
Server {
Listen 443 ssl default_server;
Listen [::]:443 ssl default_server;
Ssl_certificate /etc/nginx/ssl/netguru.crt;
Ssl_certificate_key /etc/nginx/ssl/netguru.key;
}
TLS session recovery
With HTTPS, you need to increase the TLS handshake on top of TCP. This greatly increases the time before the actual data transmission. Suppose you request /image.jpg from Warsaw and access the nearest server in Berlin:
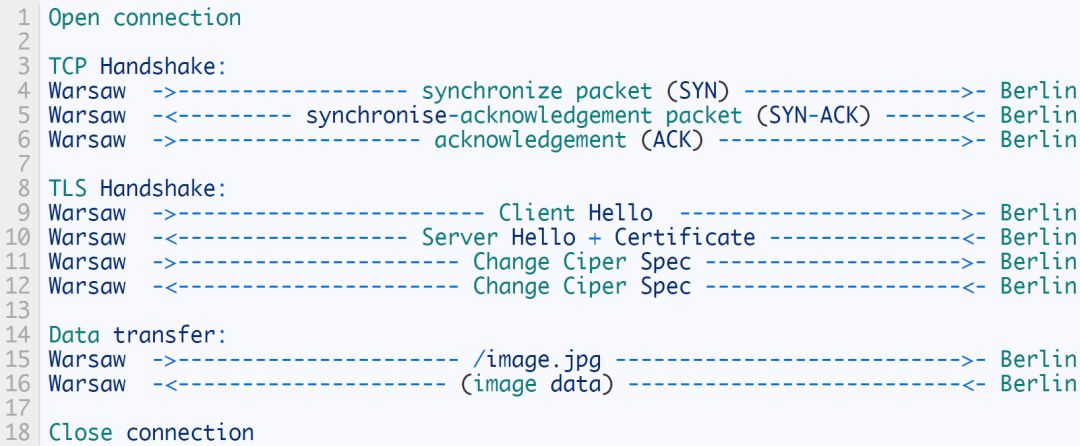
In order to save a roundtrip time during the TLS handshake and the computational overhead of generating a new key, we can reuse the session parameters generated during the first request. The client and server can store session parameters behind the session ID key. During the next TLS handshake, the client can send the session ID. If the server still has the correct entry in the cache, the parameters generated by the previous session are reused.
Server {
Ssl_session_cache shared: SSL: 10m;
Ssl_session_timeout 1h;
}
OCSP Stapling
SSL certificates can be revoked at any time. In order to know if a given certificate is no longer valid, the browser needs to perform additional queries through the Online Certificate Status Protocol (OCSP). Instead of requiring the user to perform the specified OCSP query, we can do this on the server, cache the results, and provide the client with an OCSP response during the TLS handshake. It is called OCSP stapling.
Server {
Ssl_stapling on;
Ssl_stapling_verify on; # verify OCSP response
Ssl_trusted_certificate /etc/nginx/ssl/lemonfrog.pem; # tell nginx location of all intermediate certificates
Resolver 8.8.8.8 8.8.4.4 valid=86400s; # resolution of the OCSP responder hostname
Resolver_timeout 5s;
}
Security headers
There are some headers that really deserve to be adjusted to provide greater security. For more on the headers and their details, you should definitely check the security headers of the OWASP project.
HTTP Strict-Transport-Security
Or HSTS for short, forcing the user agent to use HTTPS when sending a request to the source.
Add_header Strict-Transport-Security "max-age=31536000; includeSubdomains; preload";
X-Frame-Options
Indicates whether the browser needs to render the page in one frame, one iframe, or one object tag.
Add_header X-Frame-Options DENY;
X-Content-Type-Options
This option will prevent the browser from sniffing the file when it determines the file type. The file will be translated in the format declared in the Content-Type header.
Add_header X-Content-Type-Options nosniff;
Server tokens
Another good practice is to hide information about the web server in the HTTP response header field:
Server : nginx/1.13.2
This can be done by disabling the server_tokens directive:
Server_tokens off;
Appendix: Let's Encrypt
installation
The latest installation package can be found here.
In order to test the use of the staging environment, the rate limit is not excluded.
Generate a new certificate
Certbot certonly --webroot --webroot-path /var/ \
-d foo.netguru.co \
-d bar.netguru.co
Make sure you update properly.
Certbot renew --dry-run
Make sure you add automatic updates to the crontab. Run crontab -e and add the following line of code
3 * * * /usr/bin/certbot renew --quiet --renew-hook "/usr/sbin/nginx -s reload"
Check if SSL is working properly with ssllabs.
Mini Inverter,Mini Frequency Inverter,Compact Frequency Inverter,Ac Frequency Drive For Motor
Zhejiang Kaimin Electric Co., Ltd. , https://www.ckmineinverter.com
