0 Preface
In recent years, the popularity of the Android system has been very rapid. In the first quarter of 2013, the Android operating system accounted for more than 65% of the global smartphone market, an increase of 30.3% over the same period in 2012. However, the popularity of mobile phones has brought new problems. According to statistics, in China, one thousand mobile phones are lost every day, and after the mobile phone is lost, user privacy is easily violated. The security issues of mobile phones mainly include two categories, namely, the problem of mobile phone theft and privacy protection. This paper proposes a new set of anti-theft technology to effectively solve these two problems.
On the other hand, with the rapid development of smart phones and the rise of the Internet of Things, smart phones are promising as mobile terminals for the Internet of Things. Smartphones can be used to protect home security, such as remote video viewing via mobile phones for fire security. This type of mobile terminal using the mobile phone as the Internet of Things has not yet matured and complete solutions in the market. The main problem is the combination of software and hardware, which is difficult to implement. This article also designed a small Internet of Things, using mobile phones as mobile terminals to monitor home security in real time.
1.Android system overview
Android applications mainly include acTIviTIesservices, content, providers and broadcastreceivers. Considering the core content of this article, we will focus on the two components of acTIvity and broadcastreceivers.
1.1 AcTIvity Overview
In an application, an Activity is usually a separate screen that can display some controls that can also listen and process user events in response. Activities communicate through Intents. In the description structure of the Intent, there are two most important parts: the data corresponding to the action and action. Typical action types are: MAIN (activity portal), VIEW, PICK, EDIT, etc. The data corresponding to the action is represented in the form of a URI. For example, to view a person's contact information, you need to create an intent with action type VIEW and a URI representing the person. By parsing various intents, when navigating forward, the activity will call the startActivity(Intent myIntent) method. The system will find the activity corresponding to the Intent that best matches myIntent. After the new activity receives the notification of myIntent, it starts running.
1.2 BroadcastReceiver Broadcast Receiver
BroadcastReceiver is also the meaning of "broadcast receiver". As its name suggests, it is used to receive broadcasts from systems and applications. In the Android system, the broadcast is embodied in various aspects. For example, when the boot is completed, the system will generate a broadcast. When the broadcast is received, the function of booting the service can be realized. When the network status changes, the system generates a broadcast and receives the broadcast. Broadcasting can promptly and promptly perform operations such as saving data, and so on. Within the onReceive method, we can get the data in the Intent that comes with the broadcast. This is very important, just like the radio, it contains a lot of useful information. The broadcast mechanism in Android is very well designed. Many things need to be done by the developer personally. Now, just wait for the broadcast to inform yourself, which greatly reduces the development workload and development cycle.
2. System design
In the anti-theft system designed by the software, in addition to the popular anti-theft functions on the market (such as mobile phone positioning, card change notification, ring alarm, etc.), this paper also designed a new anti-theft data acquisition technology to control the mobile phone to enter the anti-theft. Hosting mode, in which the mobile phone can be remotely controlled to take photos in the background and upload photos of the thief to the mail, and detect the text messages and call records sent and received by the thief in real time, intercept the short message content, and forward the short message to the designated number. Obtain the sim card information of the thief, and fully grasp the information of the thief. Combined with the GPS mobile phone positioning function of this application, the thief can be identified more effectively and the stolen mobile phone can be retrieved.
In order to realize the above-mentioned anti-theft detection system, we analyze and design the mobile phone host mode detection, SMS interception and telephone recording monitoring respectively. Due to space limitations, functions such as photo uploading, alarm ringing, and GPS positioning are common in the market, and will not be described here.
2.1 Anti-theft hosting
2.1.1 Anti-theft host mode detection
In order to implement the hosted mode, the correct command must be received first, and only the commands sent by the user's previously specified security number can take effect. Other numbers cannot remotely control the user's mobile phone (as shown in Figure 1). This requires background real-time broadcast detection to see if there are correct instructions. As mentioned before, the system will issue a broadcast for anything. For the needs of this application, it only needs to respond to the broadcast sent when receiving the short message. It can automatically filter other actions, which can save the system a lot. Expenditure. In the Android system, the broadcast notification of receiving SMS is "android.provider.Telephony.SMS_RECEIVED"
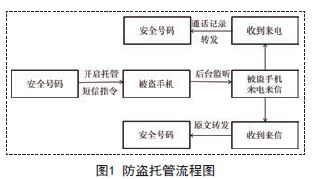
2.1.2 SMS interception and telephone recording monitoring and forwarding
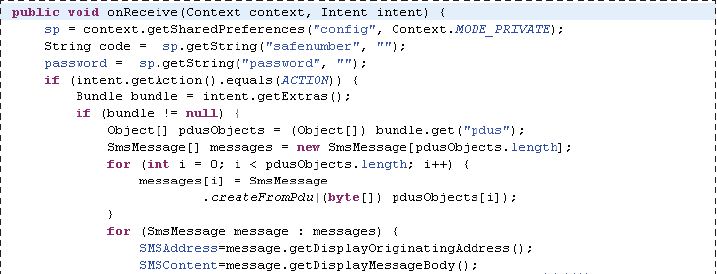
When the mobile phone receives a short message, the software will obtain the short message content and the incoming caller number in the background. If it is a secure number, it will go to the execution determination program to determine whether the content has relevant instructions. If it is a hosted command, the mobile phone automatically enters the hosted mode, and the mobile phone automatically enters the hosted mode. The phone in mode will detect whether the phone receives or sends a text message in real time, and forwards the message content and number to the security number. It should be noted that all data of the SMS first needs to be obtained through bundle.get ("pdus") and stored in the Object[] array. Here Bundle class is a keyvalue pair, the communication between the two activities can be achieved through the bundle class, the practice is: create a new bundle class, add data in the bundle class (key-value form, another activity inside the data) , you need to use the key, find the corresponding value), create a new intent object, and add the bundle to the intent object, here the intent is defined as the intent of the activity of the system to send and receive text messages. Then parse the data in the Object array to extract the SMS content and the sender number.
When the thief receives the call and makes a call, the application also detects and sends the call record to the secure number in the background. The general implementation method is to use the broadcast-Receiver to receive the specified telephone broadcast and determine the mobile phone call status. The Android platform opens three APIs for mobile phone status, namely, call, idle and ringing. Considering the needs of this application, you only need to trigger the response and get the caller number during the call. Finally, you can use SMS to Send to a secure number. The code of the application background detection and response to the SMS receiving broadcast is as follows:
Phenolic Cotton Cloth Laminated Sheet is a laminated material made by hot pressing of cotton cloths impregnated with a thermosetting phenol-formaldehyde-based binder.
Due to the use of cotton cloths, the phenolic cotton cloth mixture has high compression strength and increased resilience, favorably lends itself to machining by drilling, cutting and forging. That is why it the phenolic epoxy resin cotton cloth laminated sheets are widely used to make parts loaded with reversed electrical and mechanical stresses or working under friction (bushings, cams, etc.).
The textolite or phenolic cotton cloth sheets are used as insulating material for work in transformer oil and in the air at normal relative humidity of the environment and at 50 Hz of frequency.
Long-term allowable working temperature: -65°C to +105°С.
Phenolic cloth laminated sheet is made of cotton cloth impregnated with phenol resin, baked and hot pressed. It has high mechanical properties, oil resistance and certain dielectric properties. The heat resistance level is E level.
Phenolic Cotton Cloth Laminated Sheet
Cotton Cloth Board,Hard Cotton Cloth Board,Phenolic Cotton Cloth Board,Phenolic Cotton Cloth Laminated Sheet
Yingkou Dongyuan Electrical Insulation Board Co.,Ltd , https://www.dy-insulation.com
